WiFi Protected Access was the WiFi Alliance's direct response and replacement to the increasingly apparent vulnerabilities of the WEP standard. It was first used in 2003 and uses a 256-bit encryption model which is tough to hack. In this Wifi Hacking course you will get to know the various techniques which you can use to hack the WPA/WPA2, WEP and WPS Wi-Fi routers. The course teaches you, Wireless attack, mac spoof, AP misconfiguration, Rogue AP, War Driving, Wep Injection, Data Replay, Eavesdropping, Traffic Analysis, Evil Twin AP, DOS Attack, Beacon Flood. Wireless Network Authentication WEP & WPA. There are many authentication techniques used in various wireless network devices. These include: WEP, WPA, WPA2, WPA3, WPA2 + AES, WPA + AES, WPA + TKIP/AES, WPA + TKIP, and more. WEP and WPA are two of the most commonly used authentication techniques in a wireless network.
'Hacking Wifi' sounds really cool and interesting. But actually hacking wifi practically is much easier with a good wordlist. But this world list is of no use until we don't have any idea of how to actually use that word list in order to crack a hash. And before cracking the hash we actually need to generate it. So, below are those steps along with some good wordlists to crack a WPA/WPA2 wifi.
Note: Use the below methods only for educational/testing purposes on your own wifi or with the permission of the owner. Don't use this for malicious purposes.
So, boot up Kali Linux. Open the terminal window. And perform the following steps.
Step 1:ifconfig(interface configuration) : To view or change the configuration of the network interfaces on your system.
Here,
- eth0 : First Ethernet interface
- l0 : Loopback interface
- wlan0 : First wireless network interface on the system. (This is what we need.)
Step 2: Stop the current processes which are using the WiFi interface.
Step 3: To start the wlan0 in monitor mode.
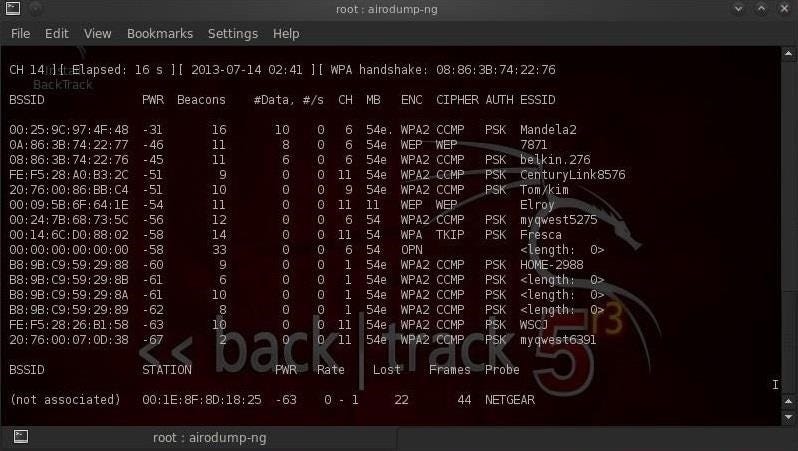
Step 4: To view all the Wifi networks around you.
Here,
- airodump-ng : For packet capturing
- wlan0mon : Name of the interface (This name can be different on the different devices)
Press Ctrl+C to stop the process when you have found the target network.
Step 5: To view the clients connected to the target network.
Here,
- airodump-ng : For packet capturing
- -c : Channel
- –bssid : MAC address of a wireless access point(WAP).
- -w : The Directory where you want to save the file(Password File).
- wlan0mon : Name of the interface.

Step 6: Open a new terminal window to disconnect the clients connected to the target network.
- aireplay-ng : To inject frames
- -0 : For deauthentication
- 10 : No. of deauthentication packets to be sent
- -a : For the bssid of the target network
- wlan0mon : Name of the interface.
When the client is disconnected from the target network. He tries to reconnect to the network and when he does you will get something called WPA handshake in the previous window of the terminal.
Now, we are done with capturing the packets. So, now you can close the terminal window.
Step 7. To decrypt the password. Open the Files application.
Here,
- hacking-01.cap is the file you need.
- aircrack-ng : 802.11 WEP and WPA-PSK keys cracking program
- -a : -a2 for WPA2 & -a for WPA network
- -b : The BSSID of the target network
- -w : Location of the wordlist file
- /root/hacking-01.cap : Location of the cap file
You can download the file of common passwords from the internet and if you want to create your own file then you can use the crunch tool
Recommended Posts:
If you like GeeksforGeeks and would like to contribute, you can also write an article using contribute.geeksforgeeks.org or mail your article to contribute@geeksforgeeks.org. See your article appearing on the GeeksforGeeks main page and help other Geeks.
Please Improve this article if you find anything incorrect by clicking on the 'Improve Article' button below.
Efforts to crack WEP encryption have been around and even publicly discussed since the inception of the WEP protocol, and this page brings you information about how to discover and calculate a WEP key from network traffic. This introduction to WEP cracking may be useful to anyone who intends to investigate network security.
Cracking WEP itself is relatively easy and can take anywhere from as little as a few minutes to a few hours (depends on the amount of network traffic, connection quality, etc.). Setting up your equipment so that it does what it needs to do can take weeks (depends on what you have and what you already know). Before you proceed to WEP cracking, read our first page of this 'tutorial' which can provide an idea about setting your computer and also about the legality of WEP cracking.
Now we can proceed to demonstrating how to crack WEP encryption.
What do I need to discover a wireless network WEP key?
Here is a list of assumptions that you need to meet in order to be able to discover a WEP key from network traffic. Note, the assumptions listed below are specific to this tutorial. Other tutorials on the web are based on different assumptions.
- Software and hardware: Ubuntu, Intel PRO/Wireless 3945ABG with the ipwraw-ng-2.3.4 driver (or alternatively TP-LINK TL-WN321G network adapter with the rt73-k2wrlz-3.0.1. driver), aircrack-ng-1.0. (Of course, you can use some other adapter as well, Intel and TP-LINK is what we used.)
- You are physically close enough to the access point to send and receive packets. Remember that just because you can receive packets from the wireless access point does not mean you will be able to transmit packets to the access point. The wireless card strength is typically less than the access point strength, so you have to be physically close enough for your transmitted packets to reach and be received by the access point.
- There is at least one wireless client connected to the network and active. The reason is that WEP cracking relies on ARP packets and if there are no active clients then there will never be any ARP request packets.
Ensure that all of the above assumptions are true, otherwise the examples that follow will not work.
We have tested WEP cracking with two network adapters: Intel PRO/Wireless 3945ABG with the ipwraw-ng-2.3.4 driver and alternatively TP-LINK TL-WN321G network adapter dongle with the rt73-k2wrlz-3.0.1. driver. The Intel adapter is referenced as wlan0 (wifi0), and the TP-LINK adapter is referenced as rausb0. You can find the name of your network adapter by executing the iwconfig command.
Does my network adapter driver work correctly?
One of the assumptions in this article is that your network interface drivers need to be patched for monitor mode and packet injection. (See the How to crack WEP with Intel PRO/Wireless 3945ABG link mentioned above for more details.)
Monitor mode testIf you loaded your driver module correctly, your network adapter might already be in Monitor mode. If it is not, try executing the following command:
sudo airmon-ng start wlan0
Wlan0 (and also wifi0) is the name of your Intel 3945 network adapter. It would be rausb0 if you worked with the TP-LINK 321. You can find the name of your network adapter by executing the iwconfig command. The print screen below shows you what you want to see in your iwconfig screen.
If the network interface is set correctly, it should say Monitor mode.
Packet injection testUse the injection test to confirm your card can inject prior to proceeding. Try executing the following two commands in your terminal window:
aireplay-ng -9 wifi0
aireplay-ng -9 127.0.0.1:666
They both should result in the 'Injection is working!' message. You can find more details here: http://aircrack-ng.org/doku.php?id=injection_test.
How WEP cracking works?
Ok, we have all the hardware and software ready, now it is time to explain how WEP cracking works.
Here are the basic steps we will be going through:
- Start the wireless interface in monitor mode
- Start airodump-ng to discover all the available networks and find your target
- Change your MAC address (optional)
- Start airodump-ng on AP channel with a bssid filter to collect the new unique IVs
- Use aireplay-ng to do a fake authentication with the target access point
- Start aireplay-ng in ARP request replay mode to inject packets
- Run aircrack-ng to crack key using the IVs collected
Sounds easy? Let's get into the details.
1. Start the wireless interface in monitor mode
If you want to listen to network traffic and to capture network traffic, your network adapter needs to be in Monitor mode. We already covered this above and also on the How to crack WEP with Intel PRO/Wireless 3945ABG page.
2. Start airodump-ng to discover all the available networks
If you want to crack WEP, you need to know a little more than just the network name. You also need to know the MAC address of the wireless access point or wireless router which you can find by executing the following command:
sudo airodump-ng wifi0
This is what you will get.
You can see names of available wireless networks in the most right column and MAC addresses of access points in the most left column. This screen also tells you how each network is secured (WEP, WPA, OPN, etc). You can also find out on which channel each access point operates.
3. Change your MAC address (optional)
In order to take advantage of the packet injection technique, you need to be associated with the target wireless access point. Many wireless networks are protected not only by WEP encryption but additionally also by MAC filtering. If that is the case with your target network, you need to first discover a MAC address of an already associated user and then use that MAC address for your own authentication and association. Read the following two pages:
How to break MAC filtering (wifi security)
How to change MAC - Macchanger
Note, you will need to disable your network adapter before changing your MAC address and then enable it again, so it is an exercise that goes through the two pages referenced above as well as through point 1 and 2 again.
Hack Wep Wifi Mac Os
How do I find a MAC address?Remember, you need to find a client on the network that is already associated with your target access point. You can do so by executing the following command in your Ubuntu terminal window:

sudo airodump-ng -c 11 --bssid 00:02:72:51:DB:28 -w wepdump -i wifi0
where -c is the channel on which your target access point is broadcasting, BSSID is the MAC address of the access point, and -w wepdump -i (we will explain later).
The screen will look similar to the screen above.
4. Start airodump-ng to collect the new unique IVs
By now, you should have all the needed information about your target access point (name, MAC, channel, etc.), your MAC address changed to the same address as some other client on the network, and your network interface set in Monitor mode. Now you want to start capturing all the new unique so-called Initialization Vectors (IVs) included in packets that go out of your access point. You can do this by starting airodump-ng on your access point channel with a BSSID filter (access point MAC address). Open new terminal window and do:sudo airodump-ng -c 11 --bssid 00:02:72:51:DB:28 -w wepdump -i wifi0
This is the same command as in step 3. We used it in step 3 to find someone that is already using your wireless access point; now we use it to capture initialization vectors. The option -w wepdump is the name of file where you want to save your initialization vectors. Option -i means that you want to save initialization vectors only and discard all other data.
The screen will look similar to the screen above in step 3.
5. Use aireplay-ng to do fake authentication with the access point
Now it is time to sort of 'login' into your wireless network. In order for an access point to accept a packet, the source MAC address must already be associated. If the source MAC address you are injecting (later) is not associated with the access point then the access point ignores the packet and sends out a 'DeAuthentication' packet in cleartext. In this state, no new initialization vectors are created because the access point is ignoring all the injected packets. The lack of association with the access point is the single biggest reason why packet injection fails. At this point you are just connecting to the access point and telling it you are here and want to talk to it. This does not give you any ability to transfer data. Open another terminal window and do:
sudo aireplay-ng -1 0 -e datel -a 00:02:72:51:DB:28 -h 00:13:CE:EC:45:20 wifi0
where -1 means fake authentication, 0 means reassociation timing in seconds, -e datel is the name of the network, -a is the access point MAC address, and -h is the MAC address under which you act (either your own or the spoofed one if you went through step 3).
This is what the output should look like.
Remember, the MAC address you target for injection must be associated with the access point by either using fake authentication or using a MAC address from an already-associated client (step 3), or both at best.
Possible problem: If you get 'Got a deauthentication packet' and then continuous retries, then you are probably dealing with MAC filtering (that is some access points are configured to only allow selected MAC addresses to associate and connect). Go back to step 3. If this is the case, you will not be able to successfully do fake authentication unless you know one of the MAC addresses on the allowed list.
Possible problem: If you get 'Waiting for beacon frame (BSSID: ...) No such BSSID available.' then you are dealing with weak wifi signal. Get closer to the access point.
Sending Authentication Request [ACK]Sending Authentication Request [ACK] that just keeps repeating on the aireplay-ng screen is another common problem. If you keep getting 'Sending Authentication Request' or 'Sending Association Request' that keep coming back, then you are too far away from the access point or are dealing with weak signal. Remember, the fact that you can capture packets from the access point does not mean that the access point can also capture packets from your computer. The signal going out of your computer is much weaker.
Also, check that you are communicating on the same wireless channel as the access point.
Another problem can be that the access point utilizes MAC addressing and your MAC spoofing in step 3 did not go right. Run the ifconfig [adapter_name] and macchanger --show [adapter_name] commands to verify your computer is communicating using MAC address of some already authenticated user. (See the download Macchanger page, 'How to verify' section for more details.)
In some cases, the access point is unable to communicate quickly enough with your computer. In this case, try to increase your delay and timing:
sudo aireplay-ng -1 6000 -o 1 -q 10 -e datel -a 00:02:72:51:DB:28 -h 00:13:CE:EC:45:20 wifi0
Some times, the fake authentication just does not work no matter what you do and you have to proceed without it.
5.1 WEP crack without packet injection
If the previous step fails in your case, and you are unable to do authentication with either a fake or your own MAC address, the next step 6 - packet injection - will likely fail too. Try it out and see. If step 6 fails, return to this section. No worry, you can still crack WEP; it will just take more time. If you are unable to authenticate and as a result do packet injection, you will be watching the screen which you opened in step 4 for a while.
Your goal is to see at least 150,000 in the #Data column. If you look at the RXQ column in the print screen above, you can see there number 49. This value provides information about the quality of your wireless connection between the access point and your computer. Anything below 80 is considered weak. If the number fluctuates a lot, you have weak signal as well.
The RXQ value relates to the data stream going from the access point to your computer. Even if this number is above 80, the access point still may not be able to see your computer. This is the most common reason for fake authentication and packet injection to fail. If that is your case, just sit back and wait until the #Data column shows at least 150,000, and then try step 7 (WEP crack). Without authentication and packet injection, this process might take 1,5 - 2 hours. You can start trying WEP crack in step 7 as soon as the #Data reaches at least 80,000, but our experience is that WEP keys usually get cracked once having somewhere around 150,000 initiation vectors.

6. Start aireplay-ng in ARP request replay mode to inject packets
To crack a WEP key for a wireless access point, we need to gather a lot of initialization vectors (IVs), ideally somewhere around 150,000 of them. Normal network traffic does not typically generate these initialization vectors very quickly. Theoretically, if you are patient, you can gather sufficient IVs to crack the WEP key by simply passively listening to the network traffic and saving them (step 5.1). Alternatively, you can use a technique called packet injection to actively speed up the process. Injection involves having the access point resend selected ARP packets (they include IVs) over and over very rapidly. This allows us to capture a large number of initialization vectors in a short period of time. So, the purpose of this step is to start aireplay-ng in a mode which listens for ARP requests then reinjects them back into the network. Open another terminal window and do:
sudo aireplay-ng -3 -b 00:02:72:51:DB:28 -h 00:13:CE:EC:45:20 wifi0
where -b is the access point MAC address, and -h is the MAC address under which you act (either your own or the spoofed one if you went through step 3).
This command will start listening for ARP requests and when it hears one, aireplay-ng will immediately start injecting it. You can generate an ARP request by pinging some other client that is already associated.
This is what the output should look like:
You can confirm that you are injecting by checking your airodump-ng and aireplay-ng screens. The data packets should be increasing rapidly. The '#/s' should be somewhere in the range of 300 to 400 data packets per second. It can as low as a 100/second and as high as a 500/second. The ARP packets and Sent packets should be increasing rapidly as well.
Step 6: Open a new terminal window to disconnect the clients connected to the target network.
- aireplay-ng : To inject frames
- -0 : For deauthentication
- 10 : No. of deauthentication packets to be sent
- -a : For the bssid of the target network
- wlan0mon : Name of the interface.
When the client is disconnected from the target network. He tries to reconnect to the network and when he does you will get something called WPA handshake in the previous window of the terminal.
Now, we are done with capturing the packets. So, now you can close the terminal window.
Step 7. To decrypt the password. Open the Files application.
Here,
- hacking-01.cap is the file you need.
- aircrack-ng : 802.11 WEP and WPA-PSK keys cracking program
- -a : -a2 for WPA2 & -a for WPA network
- -b : The BSSID of the target network
- -w : Location of the wordlist file
- /root/hacking-01.cap : Location of the cap file
You can download the file of common passwords from the internet and if you want to create your own file then you can use the crunch tool
Recommended Posts:
If you like GeeksforGeeks and would like to contribute, you can also write an article using contribute.geeksforgeeks.org or mail your article to contribute@geeksforgeeks.org. See your article appearing on the GeeksforGeeks main page and help other Geeks.
Please Improve this article if you find anything incorrect by clicking on the 'Improve Article' button below.
Efforts to crack WEP encryption have been around and even publicly discussed since the inception of the WEP protocol, and this page brings you information about how to discover and calculate a WEP key from network traffic. This introduction to WEP cracking may be useful to anyone who intends to investigate network security.
Cracking WEP itself is relatively easy and can take anywhere from as little as a few minutes to a few hours (depends on the amount of network traffic, connection quality, etc.). Setting up your equipment so that it does what it needs to do can take weeks (depends on what you have and what you already know). Before you proceed to WEP cracking, read our first page of this 'tutorial' which can provide an idea about setting your computer and also about the legality of WEP cracking.
Now we can proceed to demonstrating how to crack WEP encryption.
What do I need to discover a wireless network WEP key?
Here is a list of assumptions that you need to meet in order to be able to discover a WEP key from network traffic. Note, the assumptions listed below are specific to this tutorial. Other tutorials on the web are based on different assumptions.
- Software and hardware: Ubuntu, Intel PRO/Wireless 3945ABG with the ipwraw-ng-2.3.4 driver (or alternatively TP-LINK TL-WN321G network adapter with the rt73-k2wrlz-3.0.1. driver), aircrack-ng-1.0. (Of course, you can use some other adapter as well, Intel and TP-LINK is what we used.)
- You are physically close enough to the access point to send and receive packets. Remember that just because you can receive packets from the wireless access point does not mean you will be able to transmit packets to the access point. The wireless card strength is typically less than the access point strength, so you have to be physically close enough for your transmitted packets to reach and be received by the access point.
- There is at least one wireless client connected to the network and active. The reason is that WEP cracking relies on ARP packets and if there are no active clients then there will never be any ARP request packets.
Ensure that all of the above assumptions are true, otherwise the examples that follow will not work.
We have tested WEP cracking with two network adapters: Intel PRO/Wireless 3945ABG with the ipwraw-ng-2.3.4 driver and alternatively TP-LINK TL-WN321G network adapter dongle with the rt73-k2wrlz-3.0.1. driver. The Intel adapter is referenced as wlan0 (wifi0), and the TP-LINK adapter is referenced as rausb0. You can find the name of your network adapter by executing the iwconfig command.
Does my network adapter driver work correctly?
One of the assumptions in this article is that your network interface drivers need to be patched for monitor mode and packet injection. (See the How to crack WEP with Intel PRO/Wireless 3945ABG link mentioned above for more details.)
Monitor mode testIf you loaded your driver module correctly, your network adapter might already be in Monitor mode. If it is not, try executing the following command:
sudo airmon-ng start wlan0
Wlan0 (and also wifi0) is the name of your Intel 3945 network adapter. It would be rausb0 if you worked with the TP-LINK 321. You can find the name of your network adapter by executing the iwconfig command. The print screen below shows you what you want to see in your iwconfig screen.
If the network interface is set correctly, it should say Monitor mode.
Packet injection testUse the injection test to confirm your card can inject prior to proceeding. Try executing the following two commands in your terminal window:
aireplay-ng -9 wifi0
aireplay-ng -9 127.0.0.1:666
They both should result in the 'Injection is working!' message. You can find more details here: http://aircrack-ng.org/doku.php?id=injection_test.
How WEP cracking works?
Ok, we have all the hardware and software ready, now it is time to explain how WEP cracking works.
Here are the basic steps we will be going through:
- Start the wireless interface in monitor mode
- Start airodump-ng to discover all the available networks and find your target
- Change your MAC address (optional)
- Start airodump-ng on AP channel with a bssid filter to collect the new unique IVs
- Use aireplay-ng to do a fake authentication with the target access point
- Start aireplay-ng in ARP request replay mode to inject packets
- Run aircrack-ng to crack key using the IVs collected
Sounds easy? Let's get into the details.
1. Start the wireless interface in monitor mode
If you want to listen to network traffic and to capture network traffic, your network adapter needs to be in Monitor mode. We already covered this above and also on the How to crack WEP with Intel PRO/Wireless 3945ABG page.
2. Start airodump-ng to discover all the available networks
If you want to crack WEP, you need to know a little more than just the network name. You also need to know the MAC address of the wireless access point or wireless router which you can find by executing the following command:
sudo airodump-ng wifi0
This is what you will get.
You can see names of available wireless networks in the most right column and MAC addresses of access points in the most left column. This screen also tells you how each network is secured (WEP, WPA, OPN, etc). You can also find out on which channel each access point operates.
3. Change your MAC address (optional)
In order to take advantage of the packet injection technique, you need to be associated with the target wireless access point. Many wireless networks are protected not only by WEP encryption but additionally also by MAC filtering. If that is the case with your target network, you need to first discover a MAC address of an already associated user and then use that MAC address for your own authentication and association. Read the following two pages:
How to break MAC filtering (wifi security)
How to change MAC - Macchanger
Note, you will need to disable your network adapter before changing your MAC address and then enable it again, so it is an exercise that goes through the two pages referenced above as well as through point 1 and 2 again.
Hack Wep Wifi Mac Os
How do I find a MAC address?Remember, you need to find a client on the network that is already associated with your target access point. You can do so by executing the following command in your Ubuntu terminal window:
sudo airodump-ng -c 11 --bssid 00:02:72:51:DB:28 -w wepdump -i wifi0
where -c is the channel on which your target access point is broadcasting, BSSID is the MAC address of the access point, and -w wepdump -i (we will explain later).
The screen will look similar to the screen above.
4. Start airodump-ng to collect the new unique IVs
By now, you should have all the needed information about your target access point (name, MAC, channel, etc.), your MAC address changed to the same address as some other client on the network, and your network interface set in Monitor mode. Now you want to start capturing all the new unique so-called Initialization Vectors (IVs) included in packets that go out of your access point. You can do this by starting airodump-ng on your access point channel with a BSSID filter (access point MAC address). Open new terminal window and do:sudo airodump-ng -c 11 --bssid 00:02:72:51:DB:28 -w wepdump -i wifi0
This is the same command as in step 3. We used it in step 3 to find someone that is already using your wireless access point; now we use it to capture initialization vectors. The option -w wepdump is the name of file where you want to save your initialization vectors. Option -i means that you want to save initialization vectors only and discard all other data.
The screen will look similar to the screen above in step 3.
5. Use aireplay-ng to do fake authentication with the access point
Now it is time to sort of 'login' into your wireless network. In order for an access point to accept a packet, the source MAC address must already be associated. If the source MAC address you are injecting (later) is not associated with the access point then the access point ignores the packet and sends out a 'DeAuthentication' packet in cleartext. In this state, no new initialization vectors are created because the access point is ignoring all the injected packets. The lack of association with the access point is the single biggest reason why packet injection fails. At this point you are just connecting to the access point and telling it you are here and want to talk to it. This does not give you any ability to transfer data. Open another terminal window and do:
sudo aireplay-ng -1 0 -e datel -a 00:02:72:51:DB:28 -h 00:13:CE:EC:45:20 wifi0
where -1 means fake authentication, 0 means reassociation timing in seconds, -e datel is the name of the network, -a is the access point MAC address, and -h is the MAC address under which you act (either your own or the spoofed one if you went through step 3).
This is what the output should look like.
Remember, the MAC address you target for injection must be associated with the access point by either using fake authentication or using a MAC address from an already-associated client (step 3), or both at best.
Possible problem: If you get 'Got a deauthentication packet' and then continuous retries, then you are probably dealing with MAC filtering (that is some access points are configured to only allow selected MAC addresses to associate and connect). Go back to step 3. If this is the case, you will not be able to successfully do fake authentication unless you know one of the MAC addresses on the allowed list.
Possible problem: If you get 'Waiting for beacon frame (BSSID: ...) No such BSSID available.' then you are dealing with weak wifi signal. Get closer to the access point.
Sending Authentication Request [ACK]Sending Authentication Request [ACK] that just keeps repeating on the aireplay-ng screen is another common problem. If you keep getting 'Sending Authentication Request' or 'Sending Association Request' that keep coming back, then you are too far away from the access point or are dealing with weak signal. Remember, the fact that you can capture packets from the access point does not mean that the access point can also capture packets from your computer. The signal going out of your computer is much weaker.
Also, check that you are communicating on the same wireless channel as the access point.
Another problem can be that the access point utilizes MAC addressing and your MAC spoofing in step 3 did not go right. Run the ifconfig [adapter_name] and macchanger --show [adapter_name] commands to verify your computer is communicating using MAC address of some already authenticated user. (See the download Macchanger page, 'How to verify' section for more details.)
In some cases, the access point is unable to communicate quickly enough with your computer. In this case, try to increase your delay and timing:
sudo aireplay-ng -1 6000 -o 1 -q 10 -e datel -a 00:02:72:51:DB:28 -h 00:13:CE:EC:45:20 wifi0
Some times, the fake authentication just does not work no matter what you do and you have to proceed without it.
5.1 WEP crack without packet injection
If the previous step fails in your case, and you are unable to do authentication with either a fake or your own MAC address, the next step 6 - packet injection - will likely fail too. Try it out and see. If step 6 fails, return to this section. No worry, you can still crack WEP; it will just take more time. If you are unable to authenticate and as a result do packet injection, you will be watching the screen which you opened in step 4 for a while.
Your goal is to see at least 150,000 in the #Data column. If you look at the RXQ column in the print screen above, you can see there number 49. This value provides information about the quality of your wireless connection between the access point and your computer. Anything below 80 is considered weak. If the number fluctuates a lot, you have weak signal as well.
The RXQ value relates to the data stream going from the access point to your computer. Even if this number is above 80, the access point still may not be able to see your computer. This is the most common reason for fake authentication and packet injection to fail. If that is your case, just sit back and wait until the #Data column shows at least 150,000, and then try step 7 (WEP crack). Without authentication and packet injection, this process might take 1,5 - 2 hours. You can start trying WEP crack in step 7 as soon as the #Data reaches at least 80,000, but our experience is that WEP keys usually get cracked once having somewhere around 150,000 initiation vectors.
6. Start aireplay-ng in ARP request replay mode to inject packets
To crack a WEP key for a wireless access point, we need to gather a lot of initialization vectors (IVs), ideally somewhere around 150,000 of them. Normal network traffic does not typically generate these initialization vectors very quickly. Theoretically, if you are patient, you can gather sufficient IVs to crack the WEP key by simply passively listening to the network traffic and saving them (step 5.1). Alternatively, you can use a technique called packet injection to actively speed up the process. Injection involves having the access point resend selected ARP packets (they include IVs) over and over very rapidly. This allows us to capture a large number of initialization vectors in a short period of time. So, the purpose of this step is to start aireplay-ng in a mode which listens for ARP requests then reinjects them back into the network. Open another terminal window and do:
sudo aireplay-ng -3 -b 00:02:72:51:DB:28 -h 00:13:CE:EC:45:20 wifi0
where -b is the access point MAC address, and -h is the MAC address under which you act (either your own or the spoofed one if you went through step 3).
This command will start listening for ARP requests and when it hears one, aireplay-ng will immediately start injecting it. You can generate an ARP request by pinging some other client that is already associated.
This is what the output should look like:
You can confirm that you are injecting by checking your airodump-ng and aireplay-ng screens. The data packets should be increasing rapidly. The '#/s' should be somewhere in the range of 300 to 400 data packets per second. It can as low as a 100/second and as high as a 500/second. The ARP packets and Sent packets should be increasing rapidly as well.
Possible problem: Note, if the ARP packets count and the Sent count as well are stuck at zero, then your network interface is likely not associated with your access point. Or, you can also be too far away from the access point (weak signal).
Possible problem: Message similar to 'Got a deauth/disassoc packet. Is the source mac associated?' means you have lost association with the access point. Go back to your other window from step 5 and rerun fake authentication. This is not necessary if you went through step 3 though.
What Is Wpa Wep
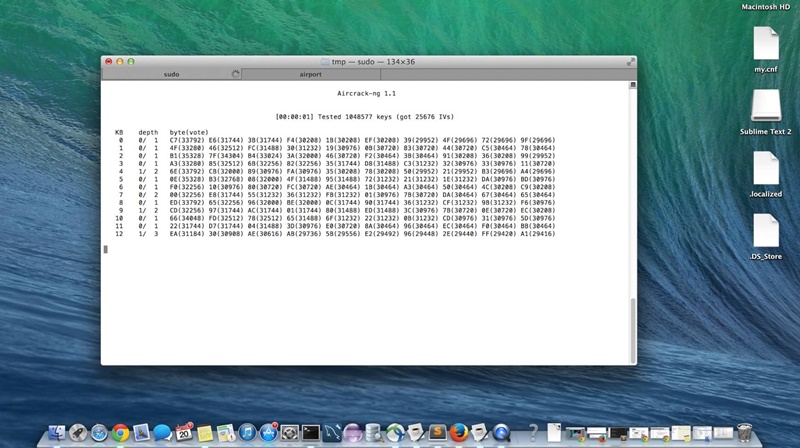
7. Run aircrack-ng to crack the WEP key using the IVs collected
Once you have captured a large number of initialization vectors, you can use them to determine the WEP key. There are two basic methods for cracking WEP: the PTW method and the FMS/Korek method.
To crack the WEP open another terminal window and execute the following commands:
sudo aircrack-ng -z -b 00:1A:92:77:BB:D9 wepdump*.ivs
sudo aircrack-ng -a 1 -0 -n 128 wepdump*.ivs
where -z invokes the PTW WEP-cracking method, -b selects the access point we are interested in, wepdump*.ivs selects all files starting with 'wepdump' and ending in '.ivs' (this comes from your airodump-ng command earlier), -a denotes FMS/KoreK attack, and -n selects the type of WEP key (128-bit in our case). These commands will calculate WEP key from the captured initialization vectors. This is what the output looks like:
You made it! Interested in more fun stuff? Read the following two articles:
How to find MAC and IP addresses in network data
How to break MAC filtering
Now that you know how to break into a WEP-protected network and therefore have discovered the weak link in your wifi network, we would also like to draw your attention to our security tutorials. We have written a few tutorials related to wireless network security. You can read more about IPSec, VPN, MAC addressing, WPA, WPA2, PSK, and many other wireless security measures. Our wireless security tutorials help you to make your network more secure.
And lastly, if you need more help with How to crack WEP, feel free to discuss in our IT discussion forum. We also suggest that you check the Related Content section in the right-hand side bar on this page. You can also find some help here:
